AWS Security Blog
Category: Management Tools
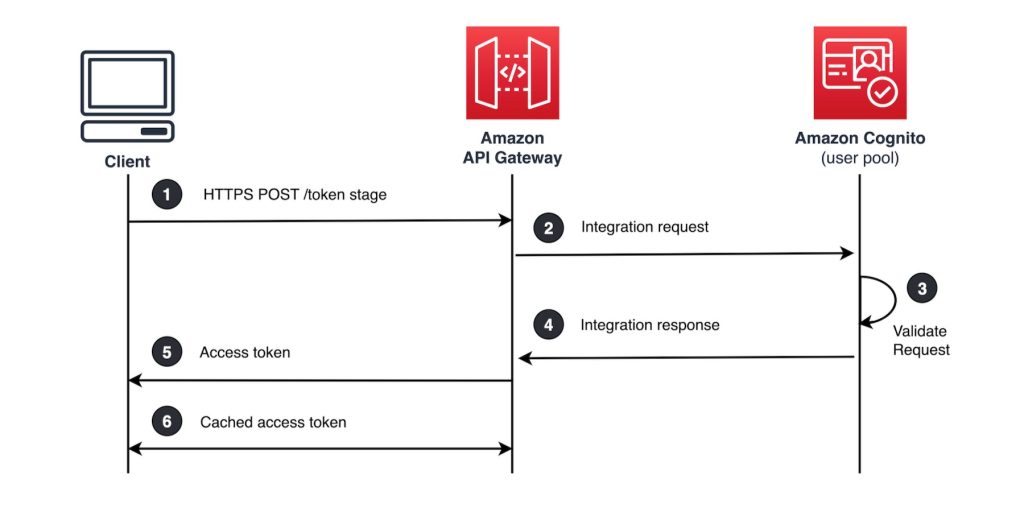
How to monitor, optimize, and secure Amazon Cognito machine-to-machine authorization
Amazon Cognito is a developer-centric and security-focused customer identity and access management (CIAM) service that simplifies the process of adding user sign-up, sign-in, and access control to your mobile and web applications. Cognito is a highly available service that supports a range of use cases, from managing user authentication and authorization to enabling secure access […]
Enforce resource configuration to control access to new features with AWS
Establishing and maintaining an effective security and governance posture has never been more important for enterprises. This post explains how you, as a security administrator, can use Amazon Web Services (AWS) to enforce resource configurations in a manner that is designed to be secure, scalable, and primarily focused on feature gating. In this context, feature […]
Generative AI adoption and compliance: Simplifying the path forward with AWS Audit Manager
As organizations increasingly use generative AI to streamline processes, enhance efficiency, and gain a competitive edge in today’s fast-paced business environment, they seek mechanisms for measuring and monitoring their use of AI services. To help you navigate the process of adopting generative AI technologies and proactively measure your generative AI implementation, AWS developed the AWS […]
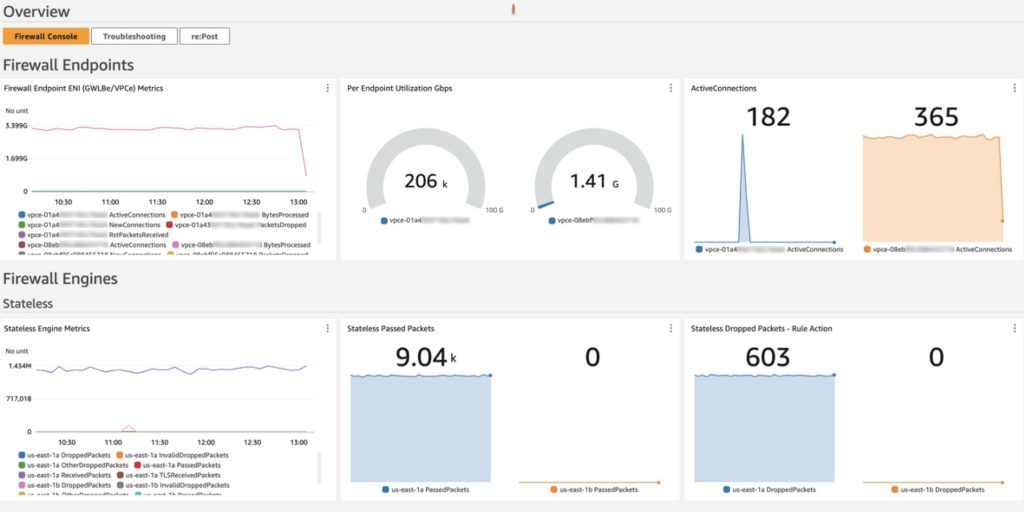
Introducing the AWS Network Firewall CloudWatch Dashboard
Amazon CloudWatch dashboards are customizable pages in the CloudWatch console that you can use to monitor your resources in a single view. This post focuses on deploying a CloudWatch dashboard that you can use to create a customizable monitoring solution for your AWS Network Firewall firewall. It’s designed to provide deeper insights into your firewall’s […]
Discover duplicate AWS Config rules for streamlined compliance
Amazon Web Services (AWS) customers use various AWS services to migrate, build, and innovate in the AWS Cloud. To align with compliance requirements, customers need to monitor, evaluate, and detect changes made to AWS resources. AWS Config continuously audits, assesses, and evaluates the configurations of your AWS resources. AWS Config rules continuously evaluate your AWS […]
Improve security incident response times by using AWS Service Catalog to decentralize security notifications
Many organizations continuously receive security-related findings that highlight resources that aren’t configured according to the organization’s security policies. The findings can come from threat detection services like Amazon GuardDuty, or from cloud security posture management (CSPM) services like AWS Security Hub, or other sources. An important question to ask is: How, and how soon, are […]
Automate detection and response to website defacement with Amazon CloudWatch Synthetics
Website defacement occurs when threat actors gain unauthorized access to a website, most commonly a public website, and replace content on the site with their own messages. In this blog post, we show you how to detect website defacement, and then automate both defacement verification and your defacement response by using Amazon CloudWatch Synthetics visual […]
Create security observability using generative AI with Security Lake and Amazon Q in QuickSight
Generative artificial intelligence (AI) is now a household topic and popular across various public applications. Users enter prompts to get answers to questions, write code, create images, improve their writing, and synthesize information. As people become familiar with generative AI, businesses are looking for ways to apply these concepts to their enterprise use cases in […]
Governing and securing AWS PrivateLink service access at scale in multi-account environments
Amazon Web Services (AWS) customers have been adopting the approach of using AWS PrivateLink to have secure communication to AWS services, their own internal services, and third-party services in the AWS Cloud. As these environments scale, the number of PrivateLink connections outbound to external services and inbound to internal services increase and are spread out […]
Use IAM Roles Anywhere to help you improve security in on-premises container workloads
This blog post demonstrates how to help meet your security goals for a containerized process running outside of Amazon Web Services (AWS) as part of a hybrid cloud architecture. Managing credentials for such systems can be challenging, including when a workload needs to access cloud resources. IAM Roles Anywhere lets you exchange static AWS Identity […]