Continuing from the previous article, Part 2 covers another case of a watering hole attack. This time, we will look at the case of a media-related website exploited in 2023. Flow of the attack Figure 1 shows the flow of the watering hole attack. When someone accesses the tampered website, an LZH file is downloaded, and when they execute the LNK file in the LZH file, their PC becomes infected...
List of “Malware”
-
-
Nowadays, many people probably recognize exploit of vulnerabilities in publicly exposed assets such as VPN and firewalls as the attack vector. In fact, many security incidents reported to JPCERT/CC also involve such devices. This is because vulnerabilities in VPN devices are exploited not only by APT groups but also by many other groups such as ransomware actors and cyber crime actors, and the number of incidents is high accordingly. As...
-
The difficult part of the initial response to a human-operated ransomware attack is identifying the attack vector. You may already know from recent security incident trends that the vulnerabilities of VPN devices are likely to be exploited, but it often takes much time to investigate because multiple penetration routes are often considered when an incident occurs. Therefore, in order to ensure a smooth initial response, it is important to investigate...
-
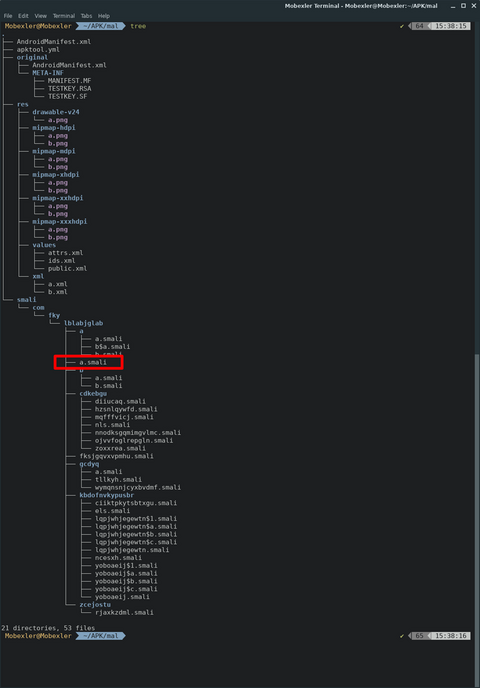
When dynamically analyzing Android malware, it is currently difficult to follow its code using debuggers unlike Windows malware. Although there is a technique [1] to hook a method dynamically by Frida [2], obtaining the in-progress state of the method is still difficult, and since Frida is not a tool dedicated to Android, only limited information can be obtained. In this article, I introduce smali gadget injection technique as a more...
-
JPCERT/CC has confirmed attack activities targeting Japanese organizations by an attack group called Kimsuky in March 2024. This article introduces the attack methods of the group confirmed by JPCERT/CC. Attack overview In the attack we identified, the attacker sent a targeted attack email impersonating a security and diplomatic organization. A zip file containing the following files with double file extensions was attached to the email. (File names are omitted.) (1)...
-
JPCERT/CC has confirmed that Lazarus has released malicious Python packages to PyPI, the official Python package repository (Figure 1). The Python packages confirmed this time are as follows: pycryptoenv pycryptoconf quasarlib swapmempool The package names pycryptoenv and pycryptoconf are similar to pycrypto, which is a Python package used for encryption algorithms in Python. Therefore, the attacker probably prepared the malware-containing malicious packages to target users' typos in installing Python packages....
-
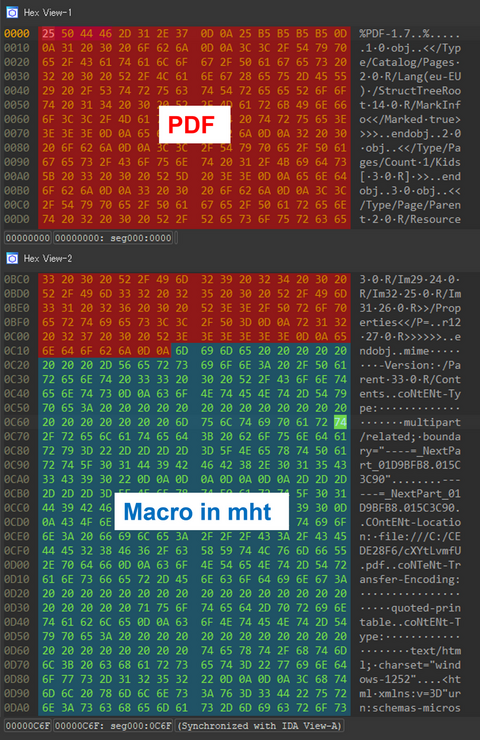
JPCERT/CC has confirmed that a new technique was used in an attack that occurred in July, which bypasses detection by embedding a malicious Word file into a PDF file. This blog article calls the technique “MalDoc in PDF” hereafter and explains the details of and countermeasures against it. Overview of MalDoc in PDF A file created with MalDoc in PDF can be opened in Word even though it has magic...
-
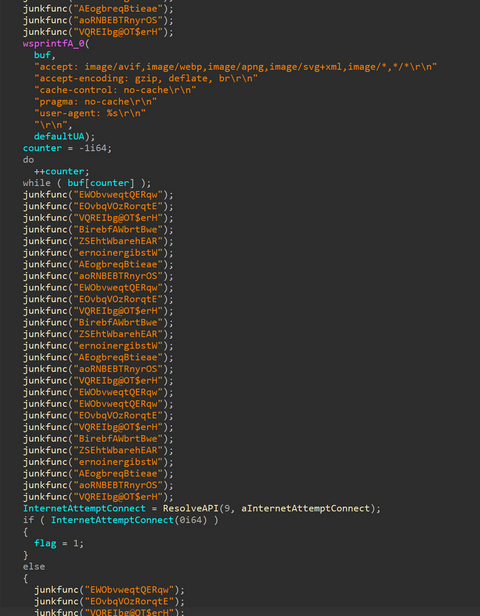
As attacks become more fileless and malware gets more obfuscated, it is getting more difficult to determine whether there is a malicious intent from a file by itself. For this reason, malware detection methods that utilize sandboxes and AI, as well as technologies that detect suspicious behavior after malware infection, such as EDR, have now become common. Even so, malware that antivirus software cannot detect is often found during actual...
-
At the end of May 2023, JPCERT/CC confirmed an attack targeting developers of cryptocurrency exchange businesses, and it is considered to be related to the targeted attack group DangerousPassword [1], [2] (a.k.a. CryptoMimic or SnatchCrypto), which has been continuously attacking since June 2019. This attack targeted Windows, macOS, and Linux environments with Python and Node.js installed on the machine. This article explains the attack that JPCERT/CC has confirmed and the...
-
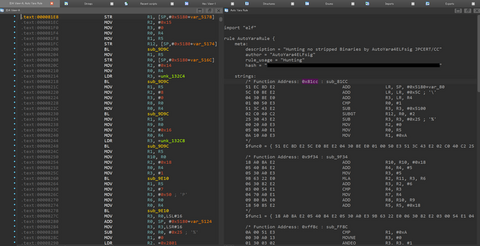
It has been observed that ELF malware removes symbol information during its build. This creates extra work in malware analysis to identify each function name because you do not know them. In addition, in IDA, an analysis tool, existing F.L.I.R.T signatures [1] (hereafter abbreviated as FLIRT signatures in this article) are often not applicable to ELF malware functions, making analysis difficult when right signatures are not found. This blog article...