
Threat Spotlight: Attacks on Log4Shell vulnerabilities
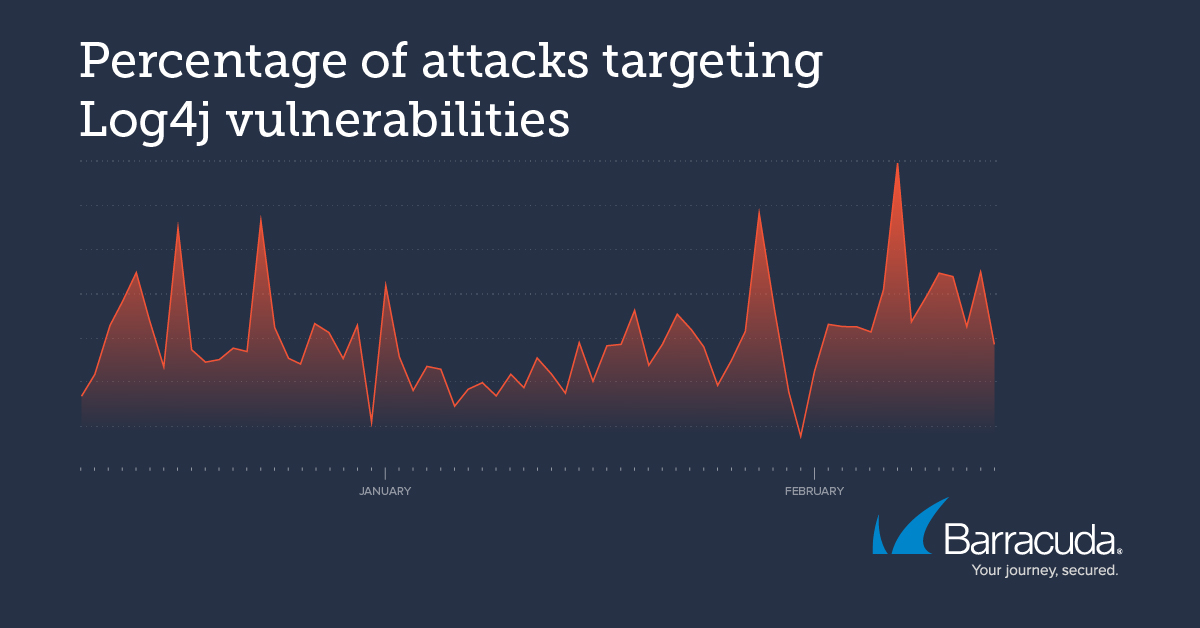
The Log4Shell complex of vulnerabilities in the Log4J software have now been publicly known for more than two months. Barracuda researchers analyzed the attacks and payloads detected by our systems since December 10, 2021, and they found that the volume of attacks attempting to exploit these vulnerabilities has remained relatively constant with a few dips and spikes over the past two months. Given the popularity of the software, the exploitability of the vulnerability and the payoff when a compromise happens, we expect to see this attack pattern continue, at least for the short-term.

Highlighted Threat
Log4Shell vulnerabilities — Log4j is a Java-based logging audit framework which is an Apache project. Apache Log4j <=2.14.1 JNDI features used in configuration, log messages, and parameters do not protect against attacker-controlled LDAP and other JNDI-related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled. The vulnerability impacts default configurations of several Apache frameworks, including Apache Struts2, Apache Solr, Apache Druid, and Apache Flink, which are utilized by numerous organizations from Apple, Amazon, Cloudflare, Twitter, Steam, and others.
The vulnerability is triggered by sending a specific string to the Log4j software which means it is simple to exploit, and the broad utilization of this software means there are multiple attack vectors.
The Details
Let’s look at a few examples of the payloads that we’ve seen attempting to exploit these vulnerabilities over the past couple of months.
For the first one, let’s look at a relatively benign (or depending on your viewpoint, very annoying) payload:
After some research, we found this Java payload:

Cryptomining payloads
The second example is something we saw a great deal of in the early days after the vulnerabilities first came to light — a Monero miner payload. It showed up from multiple different IPs, typically with the commands obfuscated in base64:


Targeting VMware installations
As time progressed, we saw reports that the Conti ransomware group was looking to compromise VMware installations using the Log4Shell vulnerabilities. Now, to our knowledge, these are mostly lateral movements from within a network. We didn’t see many examples of ransomware attacks against VMware installations and expect that this would be more an insider threat. However, while spelunking through our logs, we did see some other attempts to infect these installations. For example:


DDoS malware
For our last example, we’ll look at another type of DDoS malware:


How to protect against these types of payloads
The best way to protect against log4shell specifically is to upgrade to the latest version of log4j. Maintaining up-to-date software and libraries helps ensure that vulnerabilities are patched in a timely manner.
Due to the growing number of vulnerabilities found in web applications, it is getting progressively more complex to protect against attacks. However, all-in-one solutions are now available to protect your web applications from being exploited because of these vulnerabilities. WAF/WAF-as-a-Service solutions, also known as Web Application and API Protection (WAAP) services, can help protect your web applications by providing all the latest security solutions in one easy-to-use product.
Report: The state of application security in 2021
Subscribe to the Barracuda Blog.
Sign up to receive threat spotlights, industry commentary, and more.





