没有合适的资源?快使用搜索试试~ 我知道了~
温馨提示
内容概要:本文研究了在网络通信过程中受混合网络攻击(如欺骗攻击和拒绝服务攻击)干扰下,带有两个量化的测量信号与控制信号输出的不确定系统的弹性控制问题。针对这些情况提出了一种带量化误差和抗攻击机制的保性能弹性控制器方法,使闭合回路系统能够稳定并且符合既定的性能指标,同时解决了传感器故障以及量化带来的不确定性。为了确保控制器设计方案的有效性和可行性,进行了理论推导并给出了具体的设计条件,还通过数值模拟验证了所提方法的有效性。 适合人群:自动化控制专业研究人员或高年级学生;网络控制系统设计相关工作者。 使用场景及目标:本论文成果主要适用于涉及通信不稳定的网络环境下的工业系统,旨在保障控制系统的安全可靠运行。通过克服传输通道的限制和对抗恶意网络攻击,实现对复杂环境下不确定因素的良好鲁棒性和适应性。 其他说明:文章首先建立了数学模型来描述系统的工作状态,并详细讨论了各种干扰因素对于系统稳定性的影响。接着基于线性矩阵不等式(LMI),提出了具体的控制算法,并给出详细的证明过程。最后展示了仿真实验结果,进一步证实了新方法的有效性。文中引用了大量的现有研究成果进行对比分析,突出本文工作的新颖之处。
资源推荐
资源详情
资源评论

Received: 4 May 2022 Revised: 27 July 2022 Accepted: 17 August 2022
DOI: 10.1002/acs.3496
RESEARCH ARTICLE
Quantized output feedback resilient control of uncertain
systems under hybrid cyber attacks
Kun Yu Xiao-Heng Chang
School of Control Science and
Engineering, Bohai University, Jinzhou,
China
Correspondence
Xiao-Heng Chang, School of Control
Science and Engineering, Bohai
University, Jinzhou, China.
Email: changxiaoheng@sina.com
Summary
This article investigates the output feedback resilient control problem of an
uncertain system with two quantized signals under hybrid cyber attacks. First,
foruncertainsystems,theoutputsignal ofthesystemand theoutputsignalofthe
controllerarequantizedonce by the quantizers beforethey arepassedtothecon-
troller and the system respectively, thus affecting the signal with quantization
errorterms.Atthe same time, The adverse effects of hybridcyber attacks,includ-
ing denial-of-service attacks and deception attacks, are also taken into account
during the signaling process. In this article, a guaranteedcost resilientcontroller
design method is proposed for the above situation so that the closed-loop system
can be guaranteed to be stable or to meet the given performance index. In addi-
tion, by solving the given set of linear matrix inequalities, the design conditions
for the relevant parameters required for the resilient controller can be obtained.
Finally, the validity of the design method can be verified by simulation.
KEYWORDS
guaranteed cost control, hybrid cyber attacks, signal processing, two quantized signals, uncertain
systems
1 INTRODUCTION
Differentform the traditionaldesignated controlsystem, the networkcontrol system iscompletely distributed, connected
bythecommunication network by sensors,controllers,andactuators. Comparedwiththeformer,thenetworkcontrolsys-
tem has obvious advantages such as high applicability, high stability and low installation cost. Due to that, it has attracted
the eager attention of a large number of researchers in recent years. With more and more in-depth research, we found
that a series of problems that affect the performance of NCSs, such as signal quantized, packet dropouts, and information
transmission delay, will appear in the communication network. These problems have been discussed.
1-3
Other effects on
thesystemcanalso be observed moreintuitivelybythe filter.
4-6
Duetothefactthat in reality thereareaseriesof influences
such as temperature, humidity, and so forth, the sensors do not always work properly. Therefore, errors in signal trans-
mission due to sensor failure should be taken into account in the study. Through the research of scientific researchers, we
have learned that because of the uncertainty of the channel transmission rate state, the signal will inevitably be affected
by the quantized effect during transmission. The result is that the system state is affected to some extent, resulting in limit
cycles and chaotic behavior that degrade performance and stability. This is a problem that we urgently need to study and
solve.Therearealreadymanyliteraturesto analyze it.
7-11
Amongthe existing researcheson quantized feedbackproblems,
dynamic quantized strategies are one of the more popular ones. Compared with other quantized strategies, we assume
that the dynamic quantizer used in the dynamic quantized strategy has a time-varying effect, and dynamic parameters
2954 ©2022JohnWiley&SonsLtd. wileyonlinelibrary.com/journal/acs Int J Adapt Control Signal Process. 2022;36:2954–2970.

YU CHANG 2955
can be adjusted adaptively. In short, this quantized strategy can dynamically adjust the quantization level, which has
a good effect on reducing the limit cycle generated by the system, and at the same time can increase the attraction
area, so as to achieve the purpose of smaller impact system performance and stability. Some relevant results have been
reported.
12-16
Through analysis, this article believes that the measurement and control signals of a closed-loop system should to be
quantized due to many factors in reality. Meanwhile, observed in practice, almost all experimental subjects are uncertain
systems under the influence of uncertain factors.
17,18
Further considering that the gain in the controller will also be
affectedbyuncertainfactorsand change,in the processofsignal transmissionbetweenthefactoryand the controller,there
are disturbances that will affect the gain of the controller, so the traditional control method will appear high vulnerability.
The resilient control research based on the above uncertain system has stronger robustness and applicability, there have
been some studies in this area.
19-23
Chang et al.
20
studies the state-feedback resilient control problem for lateral motion
regulationof anintelligent vehiclein the presenceof randomlyoccurring uncertainties. In Reference21, thesampled-data
resilient control problem was solved for hybrid nonlinear stochastic systems under periodic DoS attacks.
In recent years, ensuring a certain level of performance without losing stability has become the common goal of
many scientific researchers. The guaranteed cost control strategies proposed in many literatures provide us with a more
complete design idea.
24-28
On the one hand, because of the excellent controllability of the method, the stability of the
system can be guaranteed. On the other hand, the upper limit of system performance index is given, so that the sys-
tem will be constrained by the specified upper limit during operation. At present, good results have been achieved. For
example, the guaranteed cost control problem of fuzzy coupled neural network caused by the observer framework with
Markov switching topology and external disturbances is studied in Reference 24. Robust guaranteed cost control for
polytopic parameter uncertain systems is studied in Reference 26. However, as far as we know, there are few studies dis-
cussing quantized guaranteed cost control under hybrid attacks.
29-31
Wu et al.
29
presented the guaranteed cost control
strategy of closed-loop system under hybrid network attack with two hybrid communication schemes of event trigger-
ing and time triggering. Inspired by this, the effects of quantization system with denial of service attacks and deception
attacks occurring at the same time can be considered. Deception attacks are a common attack method that uses care-
fully forged data to replace real data to achieve certain goals of the attacker.
32-34
Zhang et al.
33
focus on the problem of
designing the optimal deception attack to maximize a utility function. Static output feedback control for fuzzy Marko-
vian switching singularly perturbed systems with deception attacks and asynchronous quantized measurement output
is studied in Reference 34. Another common attack method is DoS attacks,
35-38
which directly interrupts the transmis-
sion of data in the communication channel. Wang et al.
35
focuses on dynamic output feedback control of Cyber-Physical
Systems under Denial-of-Service attacks. DoS attacks are described in detail in Reference 37. Because hybrid cyber
attacks are difficult to be estimated, this kind of research is still in its infancy, so the study in this article is even more
important.
This article studies a type of dynamic quantized guaranteed cost control problem with hybrid attacks. In this article,
the resilient control of uncertain systems, the problem of two dynamic quantizers and the effect of hybrid cyber attacks
are considered on the basis of the guaranteed cost controller designed by the predecessor. We design an output feedback
controller and a dynamic quantizer to make the closed-loop system satisfy the stability while meeting the specified the
expected performance. Therefore, the contribution of this article can be summarized as follows:
(1) In the above-mentioned guaranteed cost control problem, a hybrid cyber attacks is first considered. Taking into
account the arbitrariness of hybrid attacks, two Bernoulli distributions are used.
(2) Uncertainty in system and controller gain is considered. And include both the quantization error and the attack
function in S-Procedure.
(3) For the system with two quantizers, a quantized guaranteed cost control strategy is proposed, and the quantized
control input is included in the cost function.
In the rest part of the article, it is organized as follows. Section 2 introduce the formulation and preliminary work of
the problem. The main results are shown in Section 3. By means of the computation of LMIs, a quantized guaranteed cost
resilient control strategy based on hybrid network attack is proposed. Section 4 further illustrates the effectiveness of the
proposed strategy through simulation. Finally, Section 5 summarizes the whole article.
Notations: The notations in this article are in standard form. ⋅ is used to denote the Euclidean vector norm. > 0
meansthat isapositivedefiniteandsymmetricmatrix.E{x}representsthemean expectationof x.0anddiag{⋅}contains
an appropriate number of zero-valued and diagonal matrices, respectively.
10991115, 2022, 12, Downloaded from https://onlinelibrary.wiley.com/doi/10.1002/acs.3496 by Zhejiang University Of, Wiley Online Library on [11/01/2025]. See the Terms and Conditions (https://onlinelibrary.wiley.com/terms-and-conditions) on Wiley Online Library for rules of use; OA articles are governed by the applicable Creative Commons License
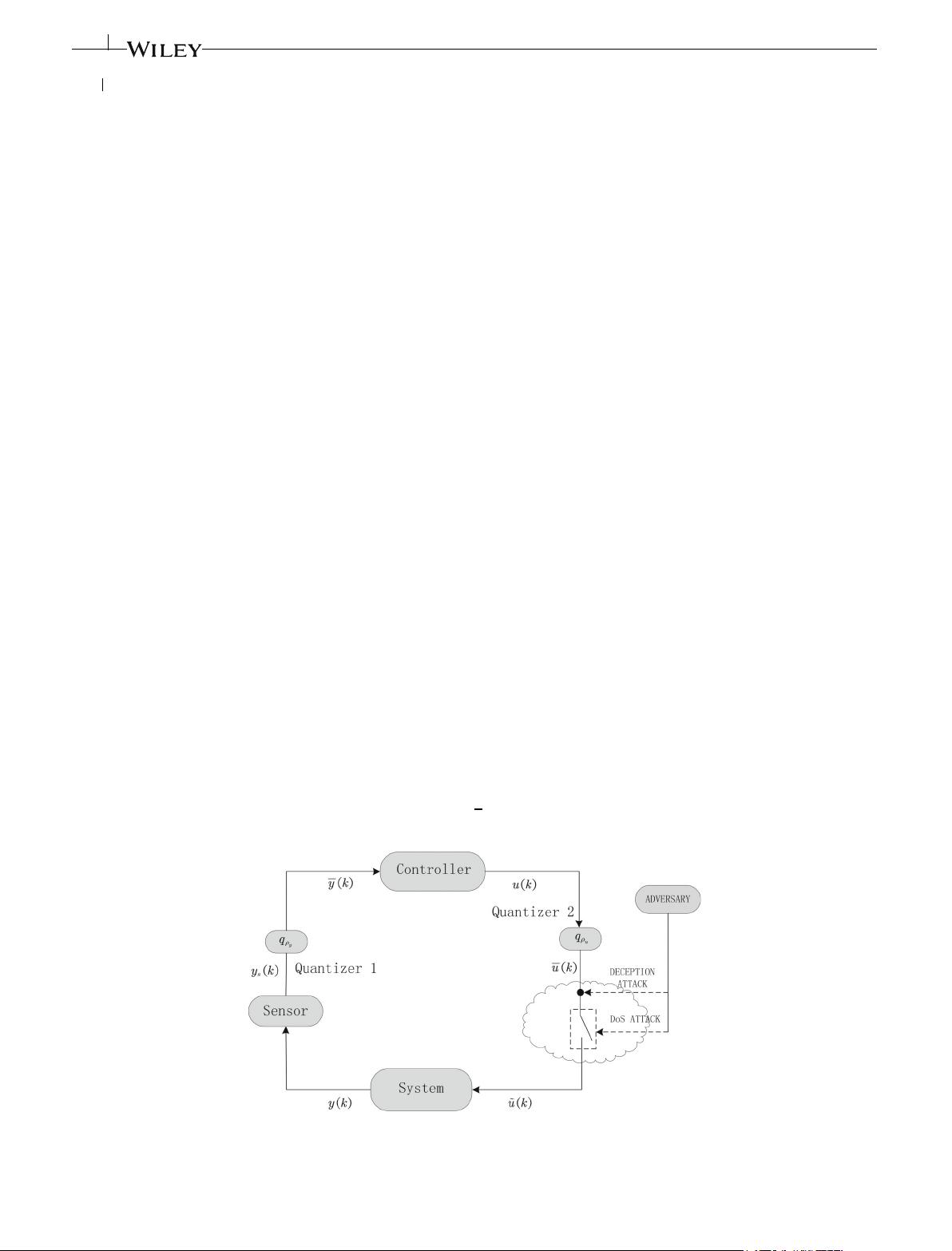
2956 YU CHANG
2 PROBLEM FORMULATION AND PRELIMINARIES
Consider a linear discrete time system with uncertainty
x(k + 1)=(A +ΔA)x(k)+(B +ΔB)
u(k),
y(k)=Cx(k), (1)
where x(k)∈
n
is the state variable,
u(k)∈
m
denotes the control input and y(k)∈
p
is represents the measurement
output. A ∈
n×n
, B ∈
n×m
,andC ∈
p×n
are known system matrices. ΔA, ΔB are unknown matrices which denote the
uncertainty in this article. The norm boundedness method is adopted to better represent them, ΔA, ΔB can be described
as ΔA = E
1
1
N
1
, ΔB = E
1
1
N
2
,whereE
1
, N
1
, N
2
are known constant matrices with appropriate dimensions, and
1
is
unknown matrix functions bounded by
T
1
1
≤I. In addition, we define = A +ΔA and = B +ΔB.
In practical applications, the work of the sensor is always affected by the environment, such as temperature, humidity
and other objective factors, so that it is not always in effective working condition. The framework of the control systems
discussed in this article is depicted in Figure 1. In this case, the data transmission is affected to some extent, and to deal
with this failure, we write the output as:
y
s
(k)=M
1
y(k), (2)
whereM
1
= diag{m
1
, m
2
, m
3
… , m
s
} is usually defined as a matrix representing sensor faults, and conforms to 0 ≤m
pl
≤
m
p
≤m
pr
≤1,p = 1, 2 … ,s andm
pl
,m
pr
areknownconstants.In ordertofacilitateunderstanding,wecansummarizethe
following threesituations, if m
pl
= m
pr
= 0, the pth sensor is complete failure; if m
pl
= m
pr
= 1, the pth sensor assembly is
fully works; if 0 < m
pl
< m
pr
< 1,it indicates thatsome components ofthe pth sensorare faulty andcannot work properly.
In addition, the specific value of pth is determined by the number of signal outputs.
Generally speaking, in most quantized output feedback control systems, whether communication channel from
the sensor to the controller or the communication channel from the controller to the actuator, there is a quantized
effect. In our previous work,
14
we defined a dynamic quantizer. Different from other quantizers, Δ represents the quan-
tizer’s quantization error bound, and M represents the quantization range. At the same time, they satisfy the following
conditions:
q(𝜏)−𝜏≤Δ, if 𝜏≤M, (3)
q(𝜏)−𝜏> Δ, if 𝜏> M. (4)
Now that the quantizer parameter is denoted by 𝜌, the dynamic quantizer can be defined as the following equation
q
𝜌
(𝜏)=𝜌q
𝜏
𝜌
,𝜌>0. (5)
FIGURE 1 Quantized output feedback control under hybrid cyber attacks
10991115, 2022, 12, Downloaded from https://onlinelibrary.wiley.com/doi/10.1002/acs.3496 by Zhejiang University Of, Wiley Online Library on [11/01/2025]. See the Terms and Conditions (https://onlinelibrary.wiley.com/terms-and-conditions) on Wiley Online Library for rules of use; OA articles are governed by the applicable Creative Commons License

YU CHANG 2957
In summary, we are ready to quantized the input and output signals of the controller, resulting in the following
quantized form.
y(k)=q
𝜌
y
(y
s
(k)) = 𝜌
y
q
y
s
(k)
𝜌
y
,
u(k)=q
𝜌
u
(u(k)) = 𝜌
u
q
u(k)
𝜌
u
. (6)
In practice, the possibility of random cyber attacks while the data is being transmitted over the channel is also consid-
ered. Let’s first consider the impact of spoofing attacks that can replace data. According to the References 39 and 40,by
using the attack signal f(⋅) in Assumption 1 to replace the normal data in the channel, similar to other attacks, it is found
that the occurrence of this attacks is also accidental. Bernoulli process is used to describe deception attacks conveniently
u(k)=𝜔(k)
u(k)+(1 − 𝜔(k))f(u(k)), (7)
where
u(k) is the information after deception attacks, f(u(k)) is the deception attackssignal which satisfies Assumption 1.
𝜔(k) is an uncorrelated random variable of Bernoulli distribution, and Prob{𝜔(k)=1}=𝜔,Prob{𝜔(k)=0}=1 − 𝜔,
where 𝜔 ∈[0, 1] is known. Meanwhile E{(𝜔(k)−𝜔)
2
}=(1 − 𝜔)𝜔 = 𝜛
2
1
is satisfied. We use 𝜔(k) to indicate whether a
deception attacks has occurred during data transmission over the network. When 𝜔(k)=1, it means that no deception
attacks occurred during the data transmission, and the data has not been replaced, so there is still
u(k)=
u(k). Otherwise,
it means that a deception attacks has occurred, and the transmitted data is replaced with
u(k)=f(u(k)).
Assumption1. The deception attackssignal f(u(k)) isa nonlinearfunction relatedto the measured output of the system,
which satisfies the following constraints
f(u(k))
2
≤Gu(k)
2
,
where G represents the constant matrix of the upper bound of the nonlinear function.
In addition, when the signal is transmitted through the network channel, we also consider the impact of the denial of
service attacks. Through relevant literatures can found that when the DoS attacks is in a dormant state, the signal is not
affected by it and can be transmitted normally in the network channel; when DoS attacks occurs, signals in the channel
are directly interrupted and cannot flow into the system. Since DoS attacks is arbitrarily activated, we use Bernoulli
distributiontorepresent.Considerthat both attacksmayoccur simultaneously whensignals are transmittedoverinsecure
channels. Therefore, the transmitted data affected by the attacks can be expressed as
u(k)=𝛾(k)𝜔(k)
u(k)+𝛾(k)(1 − 𝜔(k))f(u(k)), (8)
where 𝛾(k) is a Bernoulli variable, which satisfies E{𝛾(k)} = 𝛾,E{(𝛾(k)−𝛾)
2
}=(1 − 𝛾)𝛾 = 𝜛
2
2
.If𝛾(k)=1 means that
there is no DoS attacks, the data has not been changed, and it is still
u(k)=
u(k).If𝛾(k)=0 means DoS attacks occurred
during signal transmission, the transmitted data
u(k)=0.
Remark 1. In this article, our discussion of hybrid cyber attacks is deception→DoS attacks. In fact, it was found through
research that the priority of DoS attacks should be higher than that of deception attacks. Because after DoS attacks are
activated, all signals including deception signals in the channel cannot be transmitted normally, deception attacks are
useless at this time.
Remark 2. In fact, sensor failures and hybrid cyber attacks can degrade stability of signal transmission in closed-loop
systems, thereby affecting the performance of the controller. In this article, we consider these problems and use two
Bernoullidistributions to representrandomlyoccurring deception attacksand DoS attacks, respectively.Atthe sametime,
comparedwiththe traditional controller, the designedresilientcontrollercan handle theexternalsignalinterferencewell,
which improves the effectiveness of the controller and makes it have better applicability.
Next we will consider the controller gain design strategy in the case of fluctuation. The controller can be described as:
u(k)=(K +ΔK)y(k), (9)
10991115, 2022, 12, Downloaded from https://onlinelibrary.wiley.com/doi/10.1002/acs.3496 by Zhejiang University Of, Wiley Online Library on [11/01/2025]. See the Terms and Conditions (https://onlinelibrary.wiley.com/terms-and-conditions) on Wiley Online Library for rules of use; OA articles are governed by the applicable Creative Commons License
剩余16页未读,继续阅读
资源评论


pk_xz123456
- 粉丝: 2968
- 资源: 4150
上传资源 快速赚钱
 我的内容管理
展开
我的内容管理
展开
 我的资源
快来上传第一个资源
我的资源
快来上传第一个资源
 我的收益 登录查看自己的收益
我的收益 登录查看自己的收益 我的积分
登录查看自己的积分
我的积分
登录查看自己的积分
 我的C币
登录后查看C币余额
我的C币
登录后查看C币余额
 我的收藏
我的收藏  我的下载
我的下载  下载帮助
下载帮助

 前往需求广场,查看用户热搜
前往需求广场,查看用户热搜最新资源
- S7-200基于PLC的复杂路交通灯控制系统 带解释的梯形图程序,接线图原理图图纸,io分配,组态画面
- 基于PLC的4路抢答器控制系统的设计四路抢答 带解释的梯形图程序,接线图原理图图纸,io分配,组态画面
- 双容水箱液位PID控制设计(matlab simulink控制采用p pi pd pid 四种对比 包含说明文档
- S7-200组态王基于PLC的游泳池水处理 带解释的梯形图程序,接线图原理图图纸,io分配,组态画面
- 远景能源风机平台主控制系统
- 光伏同步发电机并网matlab simulink模型,pv-vsg 通过波形观察,运行良好 只提供模型,供参考学习
- 六轴机械臂时间能量冲击最优轨迹规划 轨迹优化 支持最高7次NURBS 默认7次 可修改成其他阶数 扩展性强 可出 关节位置 关节速度 关节加速度图 pareto最优解集图 可复现浙大机械手多目标轨迹规
- MATLAB simulink软件设计汽车七自由度整车模型的建模 有仿真结果文件和资料 下图是部分仿真
- 埃斯顿伺服驱动器源码;PCB;源理图;BOM;技术参数 埃斯顿 伺服驱动器源码;PCB;源理图;BOM;技术参数 埃斯顿 伺服驱动器源码;PCB;源理图;BOM;技术参数;资料齐全可直接生产 250
- 基于用户的协同过滤购物系统 协同过滤网上购物 协同过滤商城系统 推荐原理:根据用户拿后记录计算用户相似度,将相似度高的用户的拿后进行互相推荐 技术栈:springboot mybatis jsp my
- 西门子1200程序双相机4轴多工位检测设备,KTP700触摸屏,仅供电气编程者学习借鉴 程序主要有,上下双工位4轴脉冲控制步进电机; 与上位机双相机的TCP IP通讯;有一台第三设备的modbus r
- 基于时间和空间的大规模电动汽车入网网损调度 建立MISOCP模型,分时段优化,并行计算(实时优化) 并对比了优化和未优化结果,验证了调度的有效性 考虑到电动汽车的机动性,市区可分为三类功能区:住宅
- 异步电机无速度传感器控制仿真 全部采用sfunction搭建 可以赠送有速度传感器控制 图片为正反转转速零穿波形
- 基于matlab语音信号处理,针对采集的语音信号,观察其时域、频域波形,然后分别通过抽取,内插操作,结合处理后的时频域波形,分析了抽取与内插对信号的影响 最后分别设计了两个模拟滤波器,并利用脉冲响应
- K7+6678信号处理板 方案 原理图 pcb
- 基于fpga的qam调制解调器设计
资源上传下载、课程学习等过程中有任何疑问或建议,欢迎提出宝贵意见哦~我们会及时处理!
点击此处反馈



安全验证
文档复制为VIP权益,开通VIP直接复制
 信息提交成功
信息提交成功