
Simplified Zero Trust security with the Microsoft Entra Suite and unified security operations platform, now generally available
Microsoft Copilot for Security is now Microsoft Security Copilot.
We’re announcing new capabilities to help accelerate your transition to a Zero Trust security model with the general availability of the Microsoft Entra Suite, the industry’s most comprehensive secure access solution for the workforce, and the general availability of Microsoft Sentinel within the Microsoft unified security operations platform, which delivers unified threat protection and posture management. These innovations make it easier to secure access, identify and close critical security gaps, detect cyberthreats, reduce response times, and streamline operations.

Zero Trust in the age of AI
Watch our on-demand webinar to learn how to simplify your Zero Trust strategy with the latest end-to-end security innovations.
The extraordinary advancements in technology that make our work lives easier and more flexible also create opportunities for bad actors seeking more effective ways to launch cyberattacks. A Zero Trust strategy is vital for helping keep your organization safe in an era when cyberattacks against passwords, networks, and applications continue to increase. According to Gartner®, “AI enhancement can provide malicious code, and facilitate phishing and social engineering, which enables better intrusion, increased credibility, and more damaging attacks.”1
A proactive Zero Trust security strategy unifies defenses across identities, endpoints, networks, applications, data, and infrastructure with comprehensive security policies, pervasive threat protection, and governance. While individual tools are typically used to fulfill requirements across each Zero Trust pillar, a truly comprehensive strategy connects them together through a centralized access policy engine and integrated threat protection. This delivers defense-in-depth cybersecurity across your on-premises, hybrid, and multicloud environments.
Buying individual solutions and building truly comprehensive architecture from scratch is a herculean effort for most organizations. We’ve designed our security offering from the ground up to enable Zero Trust—delivering built-in integrations with unified policies, controls, and automation to accelerate your implementation and strengthen your security posture.
These announcements further simplify the implementation of a Zero Trust architecture across the full lifecycle from prevention to detection and response. The Microsoft Entra Suite enables organizations to converge policies across identities, endpoints, and private and public networks with a unified access policy engine. Our unified security operations platform brings together all the security signals your environment generates, then normalizes, analyzes, and uses them to proactively defend against cyberthreats.
The Microsoft Entra Suite
Given that 66% of digital attack paths involve insecure identity credentials, the Microsoft Entra Suite plays a critical role in preventing security breaches.2
Microsoft Entra adds identity skills to Copilot for Security
Read moreImplemented alone, neither identity nor network security can address all possible access scenarios. The Microsoft Entra Suite unifies identity and network access security—a novel and necessary approach for Zero Trust security. It provides everything you need to verify users, prevent overprivileged permissions, improve detections, and enforce granular access controls for all users and resources. Its native integration facilitates collaboration between identity and network teams. It also reduces your IT administrators’ workload, because they can easily manage and enforce granular identity and network access policies in one place. In addition, Microsoft Entra skills in Microsoft Copilot for Security help identity professionals respond more quickly to identity risks.

The Microsoft Entra Suite can help you do the following:
Unify Conditional Access policies for identities and networks. Security teams only have to manage one set of policies in one portal to configure access controls for both identities and networks. Now they can extend Zero Trust access policies to any application, whether it’s in the cloud, on-premises, or even to the open internet. Conditional Access evaluates any access request, no matter where it’s coming from, performing real-time risk assessment to strengthen protection against unauthorized access. And because the access policy engine is unified, identity and network teams can be confident that they protect every access point without leaving gaps that often exist between disparate solutions.
Ensure least privilege access for all users accessing all resources and apps, including AI. Identity professionals can automate the access lifecycle from the day a new employee joins their organization, through all their role changes, until the time of their exit. No matter how long or multifaceted an employee’s journey, Microsoft Entra ID Governance ensures they have the right access to just the applications and resources they need, which helps prevent a cyberattacker’s lateral movement in case of a breach. Identity professionals and business leaders have an additional layer of access control with regular, machine learning-powered access reviews to recertify access needs, ensure compliance with internal policies, and remove unnecessary permissions based on machine learning-powered insights that help reduce reviewer fatigue.
Microsoft Entra Verified ID introduces Face Check in preview
Read moreImprove the user experience for both in-office and remote workers. Employees enjoy a faster and easier onboarding experience, faster and more secure sign-in through passwordless authentication, single sign-on for all applications, and superior performance. They can use a self-service portal to request access to relevant packages, manage approvals and access reviews, and view request and approval history. Face Check with Microsoft Entra Verified ID enables real-time verification of a user’s identity, which streamlines remote onboarding and self-service recovery of passwordless accounts.
Reduce the complexity and cost of managing security tools from multiple vendors. Since traditional on-premises security solutions don’t scale to the needs of modern cloud-first, AI-first environments, organizations are seeking ways to secure and manage their assets from the cloud. With the Microsoft Entra Suite, they can retire multiple on-premises security tools, such as traditional VPNs, on-premises Secure Web Gateway, and on-premises identity governance.
Microsoft Sentinel is generally available in Microsoft’s unified security operations platform
A complete Zero Trust architecture provides effective prevention, detection, investigation, and response to cyberthreats across every layer of your digital estate. Because threat actors constantly pivot, no defense is ever absolute. That’s why taking an “assume breach” stance by continuously re-verifying every action while monitoring for new risks and threats is a Zero Trust principle.
According to our research, organizations use as many as 80 individual tools in their security portfolio. For many, this means having to manually manage integration between their security information and event management (SIEM); security orchestration, automation, and response (SOAR); extended detection and response (XDR); posture and exposure management; cloud security; and threat intelligence.
We’ve been on a journey to unify these tools over the last few years and are excited to take the next step by bringing Microsoft Sentinel into the Microsoft Defender portal, which we can announce is generally available. Microsoft Sentinel customers on the commercial cloud with at least one Microsoft Defender XDR workload deployed will now be able to:
- Onboard a single workspace into the Defender portal.
- Have unified incidents and unified hunting with Microsoft Defender XDR, streamlining their investigations and reducing context switching.
- Take advantage of Microsoft Copilot for Security for incident summaries and reports, guided investigation, auto-generated Microsoft Teams messages, code analysis, and more.
- Extend attack disruption beyond Defender XDR workloads to other critical apps—starting with SAP.
- Get tailored, post-incident recommendations on preventing similar or repeat cyberattacks that tie directly into the Microsoft Security Exposure Management initiatives to automatically improve readiness scores as actions are completed.
Microsoft Sentinel customers can adopt the new experience easily while continuing to use the classic experience in Microsoft Azure if needed. It’s never been easier to add SIEM capabilities like connectors to hundreds of data sources, and extended retention or additional compliance capabilities to your existing Microsoft Defender XDR environment.
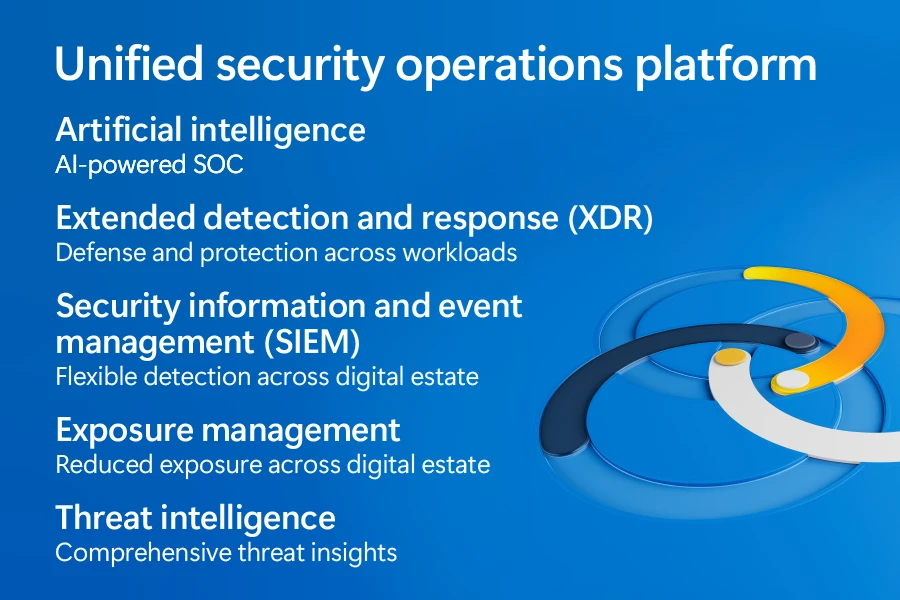
Some more details of the unified security operations platform include:
Automatically disrupt hands-on-keyboard cyberattacks with attack disruption. This out-of-the-box capability is powered by AI and machine learning to detect and stop the progression of advanced cyberattacks being conducted by well-resourced and sophisticated threat actors. Attack disruption stops the progress of human-operated ransomware, business email compromise, adversary-in-the-middle, and malicious use of OAuth apps in real time with 99% confidence, giving your security team a chance to complete their investigation and remediation under less pressure. By combining native and third-party signals from Defender XDR and Microsoft Sentinel, attack disruption has expanded to stop even more attacks in critical apps, such as SAP.
Analyze attack paths and reduce exposure. Threat actors don’t think lists, they think in graphs. Attack path management helps your security teams visualize how a cyberattacker could exploit vulnerabilities to move laterally across exposed assets in your environment. It provides guided recommendations on how they can reduce exposure and helps them prioritize actions based on each exposure’s potential impact.
Attack disruption can stop prominent cyberattacks such as ransomware in just three minutes.3
Detect and investigate faster with more accuracy. Bringing the depth of XDR signal from Defender and the flexibility of log sources from Microsoft Sentinel delivers an improved signal-to-noise ratio and enhanced alert correlation. Cyberattack timelines are automatically fully correlated in a single incident, allowing analysts to move faster to respond to breaches, with a more comprehensive view of an attack. The unification of SIEM and XDR has delivered to our customers, on average, 50% faster correlation among XDR, log data, custom detections, and threat intelligence—with 99% accuracy.3
Improved threat hunting experience. With a single experience for data querying, analysts don’t have to remember where data is available or jump across portals. Customers have found significant benefit in their ability to proactively search through data for an indicator of compromise. Embedded Microsoft Copilot for Security acts across SIEM and XDR data to further accelerate the work of security analysts with skills such as guided response or natural language to Kusto Query Language (KQL) translation.
“Our team has greatly benefited from the unified threat hunting experience provided by the platform. The integration of various data sources, including those from third-party providers through Microsoft Sentinel, has significantly enhanced our incident response capabilities. This has allowed us to expand on our threat hunting and custom detection possibilities.”
—DOW
Get started now: Commercial cloud users of Microsoft Sentinel with at least one Defender XDR workload deployed can onboard a single workspace into the Defender portal through a simple wizard, available on the home screen at security.microsoft.com. After the workspace is onboarded, customers can use the unified security operations platform for SIEM and XDR, while retaining access to their Microsoft Sentinel experience in the Azure portal.
“The biggest benefit of the unified security operations platform has been the ability to combine data in Defender XDR with logs from third-party security tools. Another advantage has been to eliminate the need to switch between Defender XDR and Microsoft Sentinel portals. We now have a single pane of glass, which the team has been wanting for some years.”
—Robel Kidane, Group Information Security Manager, Renishaw plc
Simplifying implementation of your Zero Trust architecture
By incorporating the principles of Zero Trust—verify explicitly, use least privileged access, and assume breach—the Microsoft Entra Suite and the Microsoft unified security operations platform help leaders and stakeholders for security operations, identity, IT, and network infrastructure understand their organization’s overall Zero Trust posture. They verify explicitly by ensuring continuous authentication and authorization of all access requests. They enforce least privileged access by granting only the minimal level of access necessary for users to perform their tasks, thereby reducing attack surfaces. Additionally, they assume breach by continuously monitoring and analyzing activities to identify and respond to cyberthreats proactively.
We encourage you to watch the Zero Trust spotlight on-demand, when Microsoft experts and thought leaders will dive deeper into these and other announcements, including the general availability of Microsoft Entra Internet Access and Microsoft Entra Private Access, which is part of the Microsoft Entra Suite.
Learn more about the Microsoft Entra Suite
- Read more about the general availability of Microsoft Entra Suite.
- Read more about the general availability of Microsoft Entra Internet Access and Microsoft Entra Private Access.
- Read about Microsoft Entra plans and pricing.
- Visit the Microsoft Entra Suite trial page.
- Learn more about Microsoft identity and network access solutions.
- Register for the Tech Accelerator on August 14, 2024.
Learn more about the unified security operations platform
- Combine least privileged access with endpoint management and data governance for even stronger protection of sensitive information.
- Get started with the general availability of Microsoft Sentinel in the Defender Portal with some helpful FAQs.
- Learn more about the exposure management public preview.
- Read about the new Microsoft Sentinel SOC optimization API.
- Learn more about the general availability of Microsoft Sentinel in the unified SOC platform.
- Learn about our how SOC optimization helps your organization manage costs and protections.
- Manually deploy playbooks in the unified experience.
- Compare Microsoft 365 Enterprise Plans.
- Learn about Microsoft Sentinel pricing.
Learn more about Zero Trust
- Watch the on-demand Zero Trust spotlight.
- Embrace proactive security with Zero Trust.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us on LinkedIn (Microsoft Security) and X (@MSFTSecurity) for the latest news and updates on cybersecurity.
1Gartner Survey Shows AI-Enhanced Malicious Attacks Are a New Top Emerging Risk for Enterprises, Gartner press release. May 22, 2024. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
2State of Multicloud Risk Report, Microsoft. 2024.
3Microsoft Internal Research. June 2024.

