
Google Cloud Platform allows organizations to host their data on the cloud through a variety of services including Google Compute Engine, Cloud Storage, Cloud Filestore, and much more. GCP allows you to store data, create virtual machines, host web applications, and manage data. Hosting a large amount of data on the cloud comes with its own risks. For security and privacy reasons, monitoring these resources in your cloud environment is important. This can be achieved with tools that help you collect, explore, and analyze GCP log data.
ManageEngine Log360, a comprehensive SIEM solution, provides central log management capabilities that allow organizations to store, search, monitor, analyze, and alert on log data and events in Google Cloud. With Log360, you can ingest log data from different systems, applications, and VMs, and analyze it in real time.
Log360 provides out-of-the-box reports on VPC activity, network security changes, network services, user activity, hybrid connectivity, and much more. Analyzing GCP logs can provide a deep understanding into your Google Cloud resources by pointing out changes that have occurred, who made what changes, the source IP address, and the timestamp. With this detailed information, security admins can investigate events and respond quickly.
If a security policy is modified, it can affect multiple devices, cause security and application issues, and violate compliance standards. Therefore, it's important to track the changes and identify the source in order to detect critical events in a reliable way.
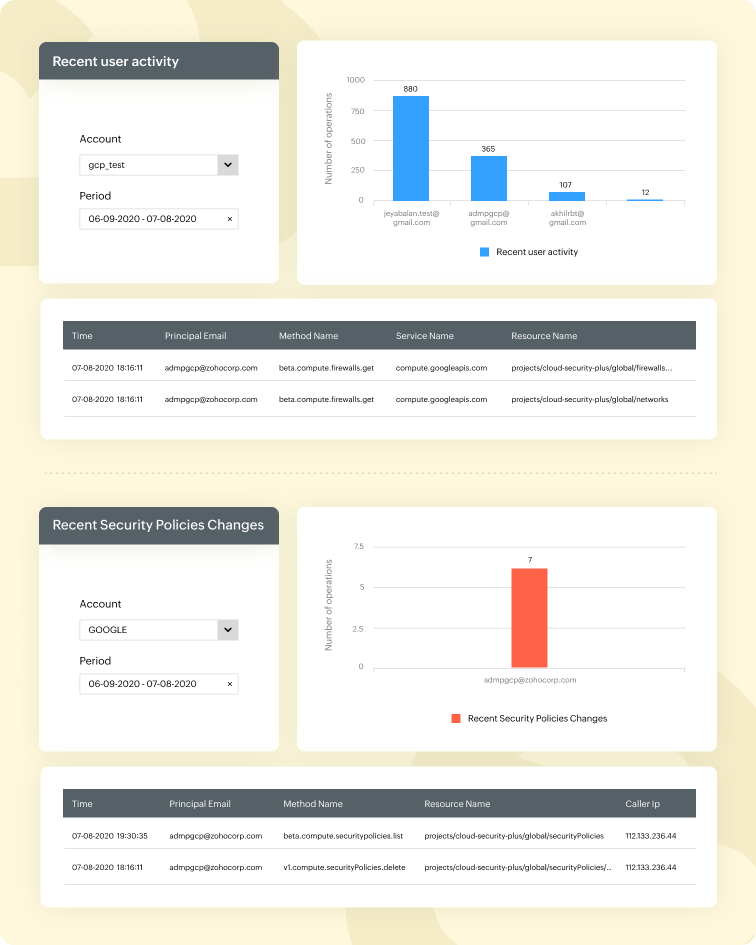
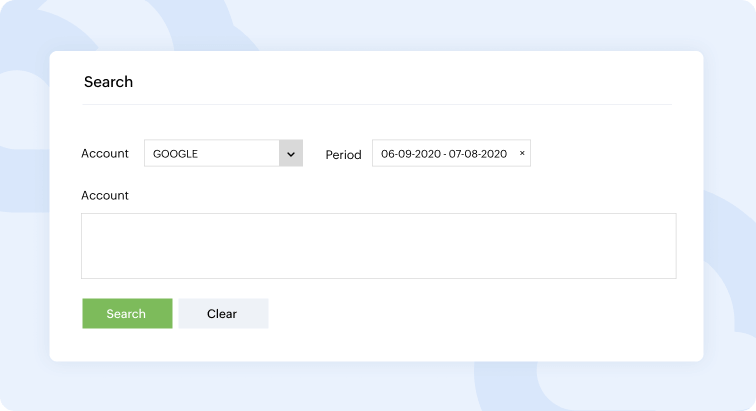
Log360 provides a powerful search engine to explore and analyze GCP logs and events, where users can search for any term related to the specific log or field. This solution also supports multiple character wildcard, phrase, grouped, boolean, and range searches.
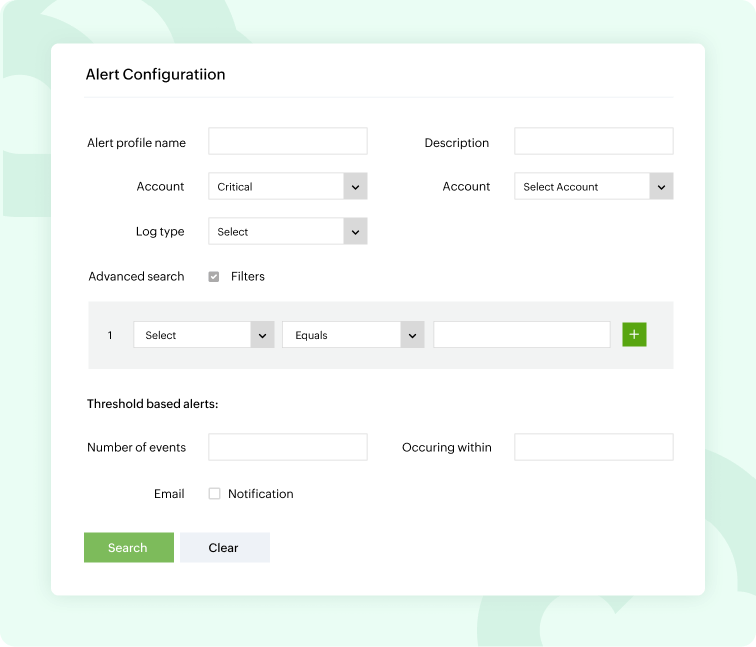
As a SIEM solution, Log360 provides organizations information on possible security threats by leveraging incident detection techniques. If a security threat is detected in your Google Cloud Platform, such as unauthorized access attempts, misconfigured resources, unusual API activity, or abnormal data transfer rates, security admins will be alerted immediately. The alerts are categorized into different levels (Attention, Trouble, and Critical) based on their severity, which helps security admins act accordingly.
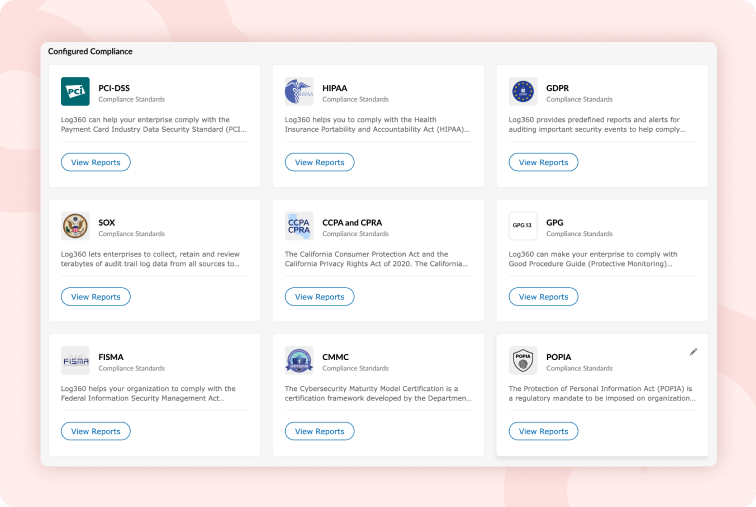
Compliance standards such as PCI DSS, HIPAA, SOX, and others require organizations to retain log data for a specified period to meet regulatory mandates. Log360 supports this by enabling you to select a custom log retention period, automating the retention process to simplify compliance. Additionally, retaining these logs is invaluable for future forensic investigations and advanced analytics.
With tools like Log360 for GCP log exploration and analytics, security teams can dive into stored logs to analyze trends, reconstruct security events, and gather threat evidence.
GCP logs are records of events and activities within Google Cloud Platform services, such as user actions, system events, and API requests. They provide insights into operations, help monitor performance, troubleshoot issues, and secure cloud resources.
The purpose of exploring and analyzing GCP logs is to gain visibility into cloud infrastructure activity, enabling detection of security threats, operational issues, and policy violations.
By analyzing logs such as audit logs, VPC flow logs, and system event logs, security teams can identify unusual behavior. This process is essential for proactive threat hunting, incident investigation, and maintaining a secure, compliant GCP environment.
Using a SIEM solution like Log360 to analyze GCP logs provides advantages beyond what GCP Log Explorer offers. While GCP Log Explorer enables exploration and analysis within Google Cloud, a SIEM centralizes logs from GCP and other environments, correlating security data across multiple sources. This comprehensive view reveals threat patterns, helps compile audit reports for compliance, and speeds up incident investigation and response.
Our ROl calculator reveals how much you can save with Log360
Calculate ROI