- Free Edition
- Quick Links
- Multi-factor authentication
- Adaptive MFA
- Active Directory MFA
- Conditional access
- Passwordless authentication
- Endpoint MFA
- MFA for remote and local Windows logons
- MFA for remote and local macOS logons
- MFA for remote and local Linux logons
- MFA for VPN logons
- MFA for OWA logons
- Offline MFA
- MFA for UAC
- Device-based MFA
- MFA for cloud apps
- MFA for Microsoft 365 users
- Phishing-resistant MFA
- Password management
- Password management and security
- Self-service password reset
- Self-service account unlock
- Web-based domain password change
- Password expiration notifications
- Password synchronization
- Password policy enforcer
- Cached credentials update
- Reporting and auditing
- Password self-service from logon screens
- Help-desk-assisted password reset
- Mobile password management
- Password security and compliance
- Single sign-on
- Remote work enablement
- Enterprise self-service
- Reporting and auditing
- Zero trust
- Integrations
- Security
- Related Products
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- EventLog Analyzer Real-time Log Analysis & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- DataSecurity Plus File server auditing & data discovery
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- AD Free Tools Active Directory FREE Tools
Understanding conditional access
The remote work model has proven to be advantageous for organizations and employees and is here to stay. As remote users are more susceptible to cyberattacks, strict security measures like MFA need to be enforced to prevent data breaches. However, applying a stringent, organization-wide access policy like MFA might have adverse effects on the user experience. While two- or three-factor authentication can secure remote logins, it might be an unnecessary hassle for on-premises users who are already secured within the perimeter of the office. A more efficient approach is to apply access policies based on context. ADSelfService Plus' conditional access feature helps achieve this. This aids organizations in:
- Implementing access controls without IT administrator intervention.
- Improving an organization's security posture without affecting the user experience.
What is conditional access?
Conditional access implements a set of rules that analyze various risk factors—such as IP address, time of access, device, and the user's geolocation—to enforce automated access control decisions. The decisions are implemented in real time based on user risk factors to avoid applying unnecessarily strict security measures in no-risk scenarios. This ensures an enhanced user experience without affecting security.
Some of the common scenarios and the corresponding security measures that can be applied using conditional access include:
- Mandating multi-factor verification for privileged users.
- Mandating MFA for off-site access to business-critical applications for all employees.
- Blocking access to high-risk actions like password reset requests from untrusted IPs or unknown devices.
How conditional access policy works in ADSelfService Plus
Basics of building a conditional access rule in ADSelfService Plus:
-
Conditions
This includes the list of factors that may make or break the security of your organization. ADSelfService Plus enables you to configure conditions based on the following risk factors:
- IP address (trusted and untrusted)
- Device (device type and platform)
- Business hours (business hours and non-business hours)
- Geolocation (based on request origin)
-
Criteria
After configuring the conditions, criteria can be devised using operators like AND, OR, or NOT. It is this criteria that is associated with the access policy.
-
Access policy
The criteria is then associated with a preconfigured access policy, referred to in ADSelfService Plus as a self-service policy. IT admins can create self-service policies and enable specific features for users belonging to particular domains, organizational units (OUs), and groups.
For more details about building conditional access rules, check out the guides on self-service policy and conditional access configuration.
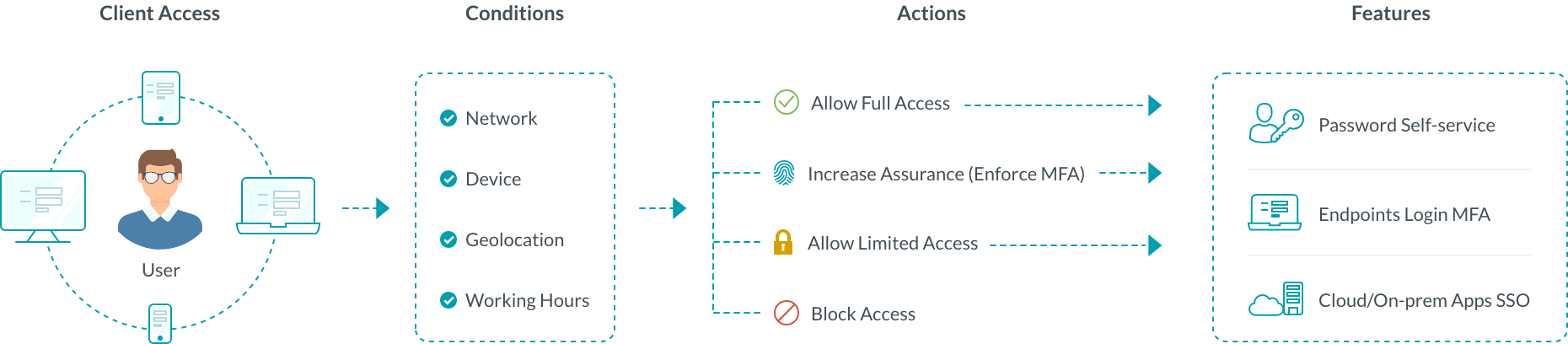
- A user logs in to their machine and tries to access an application or one of the self-service features in ADSelfService Plus.
- Based on predefined conditions, risk factors such as the user's IP address, time of access, and geolocation are analyzed.
- If the data satisfies the conditions, the user is assigned to a self-service policy that enables one of these actions:
- Complete access to the domain account and features
- Secure access using MFA
- Limited access to certain features
- Restricted access to particular features
- If the user does not satisfy any of the configured conditional access rules, a self-service policy will be applied based on the user's group or OU.
Use cases illustrating how a conditional access policy works
Use case 1: When a remote login to an organization's Active Directory (AD) domain needs to be secured using MFA
In our example, consider that on-premises users make 50% of your organization's workforce. Another 20% are remote users. The remaining 30% are users that alternate between remote and on-premises work models as required. We need to enforce MFA for users who log in remotely. Leveraging conditional access for this scenario involves:
- Enforcing a self-service policy that enables endpoint MFA.
- Configuring two conditions:
- IP address: A list of trusted IP addresses is provided.
- Location: Selecting locations outside the organization's premises.
- Creating the following criteria:
- (NOT trusted IP addresses) AND selected locations
- The criteria is associated with a self-service policy.
Here is how this conditional access policy will work:
When a user tries to log in to a machine, the user's IP address and geolocation are analyzed. If it is not a trusted IP address and a selected geolocation, the criteria is satisfied, and the user is assigned the self-service policy that enforces endpoint MFA. When the conditions aren't satisfied, any other self-service policy that applies to the user is assigned.
Use case 2: Allow only users with domain-joined machines to access enterprise applications using SSO
Enterprise applications are often used to process and store sensitive user data. Since most of these applications are now deployed in the cloud and outside the security perimeter of your network, they are a favorite target for cyberattackers. They use phishing and other attack techniques to gain access to the applications and exfiltrate data remotely. With conditional access, you can allow only users who have a domain-joined computer to access important applications that contain sensitive data. You can go one step further and permit only a list of trusted IP addresses to access critical applications, ensuring that attackers can't have access to these applications even if they steal your users' credentials. Here is an example for configuring a conditional access rule for this scenario:
- Configuring a self-service policy that enables SSO for the required applications.
- Configuring two conditions:
- IP address-based: A list of trusted IP addresses is provided.
- Device-based: All domain-joined computer objects are selected.
- Creating the following criteria:
- Trusted IP addresses AND Selected computer objects
- Associating the criteria with the created self-service policy.
Here is how this conditional access rule will work:
When a user tries to log in to an enterprise application through SSO, the device IP address and type are analyzed. If it is a trusted IP address and the computer object belongs to the AD domain, the criteria created is satisfied. Then, the self-service policy associated with the criteria is assigned to the user. This enables the user to access enterprise applications using SSO.
Benefits of enabling conditional access with ADSelfService Plus
- Choose from 20 strong authentication factors, including FIDO passkeys and biometrics, to implement MFA.
- Moderate access to machines, VPNs, OWA, RDP, and the Exchange admin center from a single console.
- Enable granular conditional access policies for different departments in the organization
FAQs
Conditional access is a security approach that restricts access to applications and data based on specific conditions, such as user location, device type, or risk level, ensuring only authorized persons receive access to applications and sensitive data.
MFA verifies a user's identity with multiple authentication methods, while conditional access assesses various conditions before granting access, allowing, or blocking based on security policies.
Conditional access should be used when access to sensitive data and applications must be given selectively and when you want to reduce the risk of unauthorized access.
Conditional access strengthens security by enforcing context-based policies, reduces unauthorized access risks, and enhances compliance with regulatory requirements
The three key elements of conditional access are the conditions, the criteria, and the access policies that will be applied to users to grant or deny access.










